On June 18th, 2012 the world record of cracked cryptology shown that even extremely difficulty and long encryption can be cracked. This effort took the team twenty one computers (252 total cores) working on the encryption for 148.2 days straight. Prior to this, scientists thought that this form of encryption would take thousands of years to defeat. To place this feat into more common terms, with the encryption utilized, there was 253 or 9,007,199,254,740,992 possibilities. So what was the solution of the key? 1752799584850668137730207306198131424550967300.
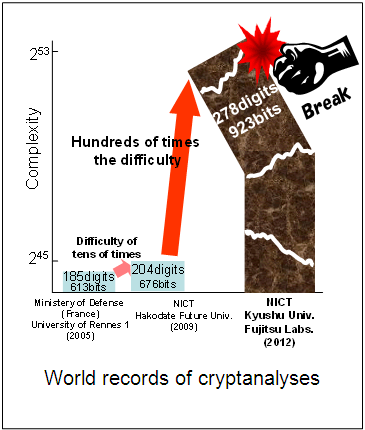 A major factor in the decrease of actual verses theorized time is the ingenuity of the team. According to Fujitsu, they “a technique optimizing parameter setting that uses computer algebra, a two dimensional search algorithm extended from the linear search, and by using our efficient programing techniques to calculate a solution of an equation from a huge number of data, as well as the parallel programming technology that maximizes computer power.” Another factor is the vast increase in processing power and memory technologies.
A major factor in the decrease of actual verses theorized time is the ingenuity of the team. According to Fujitsu, they “a technique optimizing parameter setting that uses computer algebra, a two dimensional search algorithm extended from the linear search, and by using our efficient programing techniques to calculate a solution of an equation from a huge number of data, as well as the parallel programming technology that maximizes computer power.” Another factor is the vast increase in processing power and memory technologies.
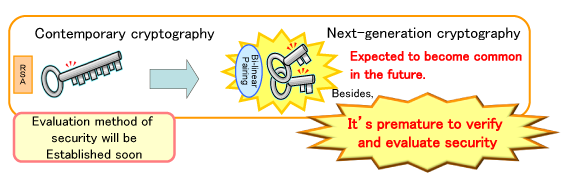
What does this mean for the future of information security? Several benefits come out of this discovery. The immediate effect is the discovery of the actual level of security in current cryptography protocols. More importantly, this provides extremely valuable analytical data to build the next generation of encryption.
 Courtesy of NICT
Courtesy of NICT
Currently, the primarily discussed next generation of public key encryption by these three organizations is pairing-based. Theorized this encryption technique based on the ability of discrete logarithm problem (DLP) to interact with each other. Looking at the general DLP equation, a = gd utilizing a public and private key could obtain extremely high bit-rate encryption. Utilizing this technology, three distinct possibilities are being looked at are identify-based encryption, keyword searchable encryption, and functional encryption.
While the security technologies are constantly evolving and becoming better, events such as these remind us that evolution is a necessity. Fortunately, researchers are working on complex mathematical equations and techniques to keep our data relatively safe for years to come.

No comments:
Post a Comment