With the advance designs in malware, phishing scams, and unintentional software security flaws, it is extremely important to maintain strong vigilance. The major factor of this is the vast expansion of users that are now on the Internet. More money can be made by these malicious users than ever before. Fortunately, with several basic steps and pieces of key knowledge, you can safely traverse through the largest network in the world, the internet.
1) Solid Anti-Malware Software
It seems to be common sense these days, but anti-malware software is a necessity on any personal computer. A good software actively scans all network communication including the following:
- Web & Scripts
- Protects against viral images and scripts designed to execute malicious code utilizing security holes in browser and operating system software.
- Mail
- Protects against malicious E-mails, scripts, and viral images.
- Some track, and detect potential Phishing scams as well.
- Works only for POP3, or IMAP email. (Loaded in an external mail program.
- Gmail, Yahoo, and Live mail would be covered using the Web & Scripts application.
- Peer 2 Peer
- Protects against communications using peer to peer connections.
- Instant Messenger
- While it is much less frequent than in previous years, exploits could be executed by using instant messenger programs such as Yahoo Messenger, ICQ, Microsoft Live, and AOL Instant Messenger (AIM).
- Resident Execution Scanners
- Detects active programs for malware activity
- Network
- Determines traffic on the local network that reaches your computer.
- Often infected computers will attempt to spread the malware throughout the entire network.
As well, look for software that provides malware database updates at least four times a week. This information is not publically available, yet once you begin using the software it will become self evident. Maintaining the program version up to date, and the database are the most important aspects of utilizing anti-malware software. Without any updates, it becomes useless.
Great examples of anti-malware software are Avast Anti-virus, and AVG.
2) Keep Windows and Internet Software Updated
Security flaws are consistently evolving due to malicious individuals finding new ways to move beyond existing security. As a result, Microsoft consistently updates their operating system and critical software such as Internet Explorer (IE) often. Unless there is an absolute critical security alert, Microsoft will push security and bug fixes live to the public on Tuesdays. An entire team is devoted to detecting and repairing security loopholes to attempt to maintain data integrity of their millions of customers. If one does not perform routine software updates, they will never gain from the benefits of these security updates.
All software that access the internet should be always the current version. This includes, but is not limited to:
- Internet Browsers
- Internet Explorer
- Firefox
- Chrome
- Safari
- Opera
- Flash, Shockwave & Silverlight
- Flash & Shockwave have been strongly targeted for maliciously injected code over the past year.
- Email Clients
- Outlook
- Eudora
- Peer to Peer Clients
- These clients are notorious for spreading viral information. Please use for legal reasons, and at your own peril.
- Online Games
- Such as Online Poker, or other free software.
- Prior to installing, ensure you thoroughly malware scan to ensure file integrity.
- Such as Online Poker, or other free software.
3) Do Not Open Unknown Links or E-mails
This falls along the same lines that your parent’s have taught you from very young, don’t talk to strangers. If you are unsure of the link or Email, do not click on it. Often, malicious individuals will create mass Emails, false webpages, or both to attempt to gain access to your computer, or personal information. With good anti-malware protection you can often avoid these instances, the software is not 100% fool proof. It is often a good idea to hover your mouse over a web link, and look at the status bar to ensure the link is the same. As an example,
Click to Enlarge
4) Ensure Site is Legitimate
While it seems like common sense, there are many sites that attempt to duplicate popular websites to gather your information. Once you enter your personal data, it is often swept away into a database and sold to a large quantity of identity thieves. For this reason, it is extremely important to ensure the site you are on is real. A general rule of thumb, if there is doubt, don’t fill it out.
A major sign of a valid website are Secure Socket Layer (SSL) certificates. This is typically only common on bank sites, but even social media sites such as Facebook and Twitter have joined the SSL movement. SSL is a method of sending data securely over an encrypted path, commonly at 128 bits. Valid SSL certificates are maintained by a third party company to ensure the sanctity of the SSL connection. Since there are only a few trusted SSL Certificate Authorities on the internet web browsers accept, it is extremely difficulty to create a false valid certificate. The following will display how a valid and invalid certificate will appear:
Click to Enlarge
You will notice that the browsers change the color of their bar to either green, or blue. This depends upon the browser and the level of security. Currently, Twitter has a higher level of secured certificate than Facebook.
Example of bad certificate in Chrome:
Click to Enlarge
Example of bad certificate in Internet Explorer
Click to Enlarge
Example of a bad certificate in Firefox
Click to Enlarge
Chrome, and Internet Explorer are very direct in displaying an invalid certificate. Currently, Firefox does allow the page to load with only a small blue symbol prior to the address bar.
A secondary way to ensure validity of a website is to check the registrar of domains. Essentially, when a domain name, (Example: Google.com) is purchased, there is public record of who purchased it. For this, you need to go to a valid registrar, and type in the address. The following is an example of Google.com’s Who Is registrar:
Click to Enlarge
A Who Is forum is available at Network Solutions.
While no method is one hundred percent fool proof, these methods should assist you in maintaining a clean, and secure computer. As with all things in life, allow your common sense and gut instinct lead as you journey through cyberspace.









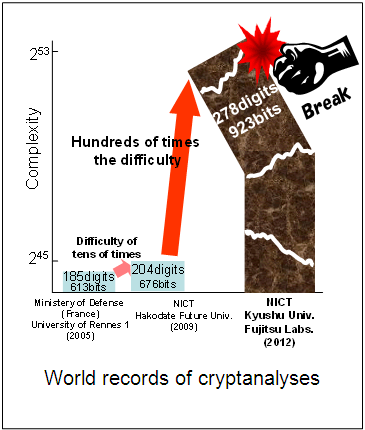 A major factor in the decrease of actual verses theorized time is the ingenuity of the team. According to Fujitsu, they “a technique optimizing parameter setting that uses computer algebra, a two dimensional search algorithm extended from the linear search, and by using our efficient programing techniques to calculate a solution of an equation from a huge number of data, as well as the parallel programming technology that maximizes computer power.” Another factor is the vast increase in processing power and memory technologies.
A major factor in the decrease of actual verses theorized time is the ingenuity of the team. According to Fujitsu, they “a technique optimizing parameter setting that uses computer algebra, a two dimensional search algorithm extended from the linear search, and by using our efficient programing techniques to calculate a solution of an equation from a huge number of data, as well as the parallel programming technology that maximizes computer power.” Another factor is the vast increase in processing power and memory technologies. Courtesy of
Courtesy of